Introduction
In today’s data-driven world, how we store, manage, and secure information is central to innovation, security, and business success. For decades, traditional databases have been the cornerstone of digital information systems, enabling everything from banking to healthcare to logistics. However, the emergence of blockchain technology has introduced a novel approach that challenges long-standing database models and introduces entirely new paradigms of trust, transparency, and decentralization.
While both blockchain and traditional databases are tools for storing data, their fundamental architectures, control mechanisms, and intended purposes differ significantly. Blockchain is not a replacement for traditional databases in all cases but rather an alternative suited to specific types of problems, especially those requiring trustless cooperation among multiple parties. This article explores, in detail, the core differences between blockchain and traditional databases in terms of structure, governance, performance, security, use cases, and their broader implications for digital infrastructure.
1. Architecture and Design Philosophy
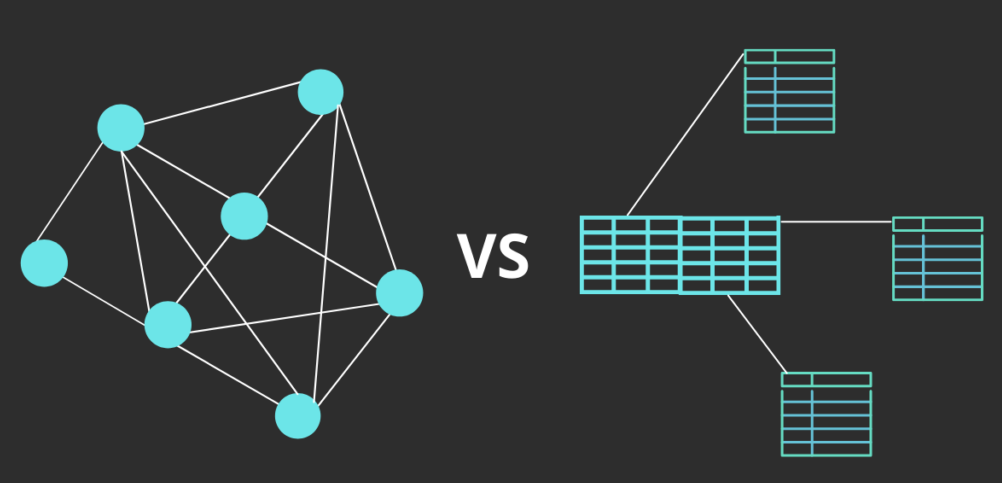
One of the most important distinctions between blockchain and traditional databases lies in their architecture. Traditional databases are centralized systems controlled by a single authority, whereas blockchains are decentralized and distributed across a network of nodes.
A traditional database, such as those using the relational model (e.g., MySQL, PostgreSQL), stores data in structured tables where records can be queried, updated, or deleted. This model relies on trust in the central system administrator or organization to manage the data fairly, securely, and accurately.
In contrast, blockchain systems are designed to function in an environment where trust is minimal or nonexistent. A blockchain is a decentralized ledger of transactions maintained by a network of participants, often referred to as nodes. Each participant maintains a copy of the entire ledger, and changes to the ledger require consensus from the network. The core design principle of blockchain is that no central authority is necessary; instead, cryptographic protocols and consensus mechanisms ensure the integrity and consistency of the data.
2. Data Structure
Traditional databases organize data using well-established models like relational, document, key-value, or graph-based systems. These databases offer flexibility and efficiency for storing and querying structured and semi-structured data. They allow users to perform Create, Read, Update, and Delete (CRUD) operations easily.
Blockchains use a fundamentally different structure. Data is stored in blocks, and each block contains a list of transactions. Each new block is linked cryptographically to the previous one, forming an immutable chain. Once data is added to the blockchain and confirmed by the network, it cannot be altered or deleted. The structure of blockchain is thus linear and append-only.
This immutability is one of the defining characteristics of blockchain. It guarantees the integrity of past transactions and provides a verifiable history of all actions on the network. However, it also limits flexibility. You cannot simply “delete” or “edit” a record; instead, you must append a new transaction to reverse or modify previous ones.
3. Control and Access
Traditional databases are typically owned and controlled by a single entity. The database administrator or the hosting organization manages user access, defines roles and permissions, and governs how data is handled. In most cases, access to the database is restricted to internal systems or verified external users. Trust in the administrator or the institution is a requirement.
Blockchains, especially public blockchains, operate in a trustless environment. Anyone can participate in the network without needing approval from a central authority. Instead of role-based access control, blockchain relies on network consensus to validate new entries. Each node on the blockchain network has equal authority, and changes to the data must be agreed upon through a consensus algorithm.
Private blockchains and permissioned blockchains introduce variations of control, allowing some degree of centralized governance while retaining certain decentralization principles. These are often used in enterprise settings where regulatory or performance constraints exist.
4. Consensus Mechanisms
Traditional databases do not require consensus mechanisms because they are managed by a central authority. Data is assumed to be accurate as long as it is written or modified by authorized users. Conflict resolution is handled internally, often through transactions and locking mechanisms that ensure data consistency.
Blockchain, however, requires a mechanism for all participants to agree on the state of the ledger. This is achieved through consensus algorithms such as Proof of Work (PoW), Proof of Stake (PoS), or Practical Byzantine Fault Tolerance (PBFT). These mechanisms ensure that all copies of the ledger remain in sync, even when some nodes might behave maliciously or go offline.
Consensus is critical for maintaining data integrity in a decentralized system. It allows blockchains to remain secure and trustworthy without centralized control, but it also introduces significant computational and temporal costs. For instance, PoW (used by Bitcoin) requires enormous amounts of energy and computing power, making it slow and expensive.
5. Data Immutability and Auditability
A major difference between the two technologies is how they handle historical data. Traditional databases allow data to be modified or deleted. Although logs and backups can be maintained for audit purposes, these are not inherently tamper-proof. A malicious administrator or hacker with sufficient access can manipulate data or erase traces of wrongdoing.
In contrast, blockchain provides native immutability. Once a transaction is written to the blockchain and validated by the network, it becomes nearly impossible to change. This makes blockchains ideal for audit trails, financial records, supply chain tracking, and other use cases where transparency and accountability are critical.
Immutability is a double-edged sword. It enhances security and accountability, but it also makes error correction difficult. Mistaken transactions cannot be reversed unless the system allows for compensating entries, and even then, the original transaction remains visible and permanent.
6. Performance and Scalability
Traditional databases are optimized for performance. They can handle thousands or millions of transactions per second, depending on hardware and configuration. They support complex queries, indexing, and caching to improve response times and scalability.
Blockchains, by contrast, are comparatively slow and inefficient in terms of transaction throughput. Each transaction must be broadcast to the entire network, validated, and written into a new block. The rate at which new blocks are added is limited by consensus algorithms and block size. For example, Bitcoin processes about seven transactions per second, while Visa processes thousands.
Scalability is one of the major challenges facing blockchain technology. Solutions such as sharding, Layer 2 protocols (like Lightning Network), and sidechains are under development to address this issue, but these introduce additional complexity and potential security concerns.
7. Security, Fault Tolerance, and Resilience
Traditional databases depend heavily on security measures such as firewalls, encryption, access controls, and intrusion detection systems. However, because they are centralized, they have a single point of failure. If the central server is compromised or goes offline, the entire database can become unavailable or corrupted. Recovery mechanisms such as backups and disaster recovery plans are essential but can be complex and time-consuming.
Blockchain’s distributed nature enhances fault tolerance. Because copies of the ledger are stored on multiple nodes across a network, the failure or attack on some nodes does not compromise the overall system. The use of cryptographic hashes, digital signatures, and consensus protocols further strengthens security, making blockchain resistant to tampering and fraud.
However, blockchains are not immune to risks. Public blockchains face threats such as 51% attacks, where a malicious actor controlling the majority of computing power could alter the ledger. Private blockchains may be vulnerable if governance is weak or if insiders act maliciously.
8. Privacy, Confidentiality, and Transparency
Traditional databases excel at protecting sensitive information. Through access control, data masking, encryption, and strict privacy policies, sensitive data can be tightly guarded. This makes them suitable for environments such as banking, healthcare, or government where privacy is paramount.
Blockchains—particularly public ones—are inherently transparent. All transactions are recorded on a public ledger accessible to everyone. While users’ identities are pseudonymous (represented by cryptographic keys), transaction details are visible, which can raise privacy concerns.
To address this, several solutions have emerged such as permissioned blockchains restricting who can access data, zero-knowledge proofs that verify data without revealing it, and privacy-focused blockchains like Monero or Zcash that use advanced cryptographic techniques.
9. Regulatory and Legal Considerations
Traditional databases operate under established regulatory frameworks. Compliance with laws such as GDPR, HIPAA, and Sarbanes-Oxley is well understood and integrated into database design and management. Data can be deleted or modified to comply with regulations like the “right to be forgotten.”
Blockchain’s immutability presents challenges in this regard. For example, once personal data is recorded on a blockchain, it cannot be deleted or altered, potentially conflicting with GDPR requirements. Legal frameworks are still evolving to accommodate these new realities.
Furthermore, blockchain’s decentralized nature raises questions about jurisdiction, liability, and governance. Determining who is responsible for data on a global, permissionless blockchain is complex, requiring new approaches in law and policy.
10. Use Case Comparisons
Traditional databases remain the optimal solution for many applications requiring fast, flexible, and private data handling—such as enterprise resource planning, customer relationship management, and content management systems.
Blockchain shines in scenarios where trust between multiple parties is limited or absent, where transparency and auditability are essential, or where decentralization provides unique benefits. Common use cases include cryptocurrency, supply chain tracking, decentralized finance (DeFi), digital identity verification, and secure voting systems.
Hybrid approaches are also emerging, combining blockchain’s immutable audit trails with traditional databases’ efficiency and flexibility to optimize for specific needs.
11. Philosophical and Ideological Differences
Traditional databases reflect a centralized worldview where trust is placed in institutions, administrators, or corporations to safeguard data and act responsibly.
Blockchain represents a shift toward decentralization and trustlessness, empowering individuals and communities to control their data and transact without intermediaries. This paradigm aligns with broader movements toward democratization, censorship resistance, and user sovereignty on the internet.
Conclusion
Although blockchain and traditional databases both manage data, they differ fundamentally in architecture, control, performance, security, and philosophy. Traditional databases prioritize efficiency, flexibility, and privacy within trusted environments. Blockchain emphasizes decentralization, immutability, and transparency in trustless settings.
Neither technology is universally better; instead, each suits particular contexts and requirements. Understanding their differences enables businesses, developers, and policymakers to make informed decisions about when and how to deploy these technologies to maximize value and innovation in the digital age.













































